As anyone who has toured our data centers knows, our purpose-built facilities are extremely secure, and security procedures are strictly enforced. Though we’ve met PCI DSS requirements since Texas 1 opened for business in 2011, we are now officially certified by a third party for meeting PCI DSS requirements.
The Importance of Third-Party PCI DSS Compliance
Understandably, it’s more difficult to trust data center operators that claim to be PCI compliant based on their own audits. This leaves companies to do their own audits when considering a new data center for their IT infrastructure. Third-party audits are objective and provide reports and certifications to verify that data centers meet all requirements, resulting in less work for companies to perform when doing their due diligence before selecting a new data center.
PCI DSS Compliance Requirements for Data Centers
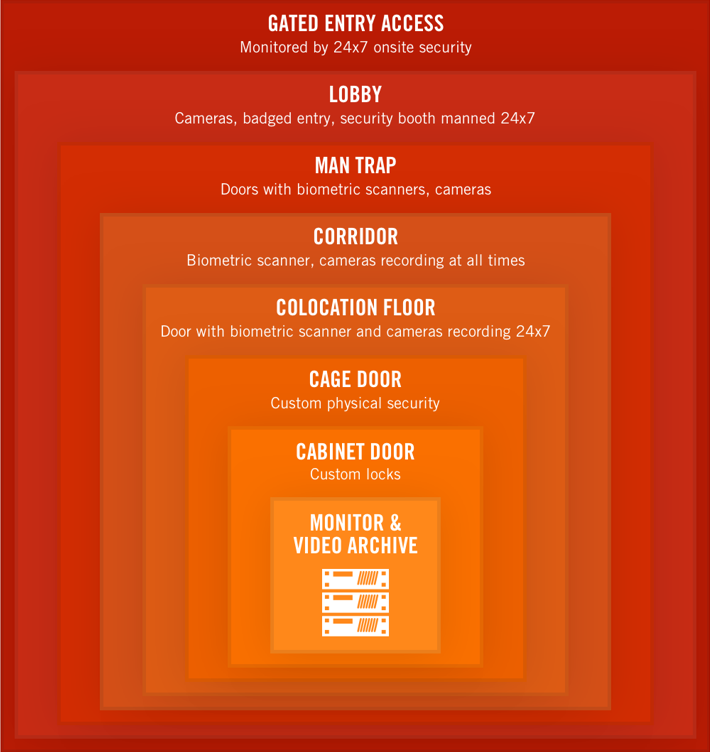
Most PCI DSS requirements for data centers have to do with physical security and security procedures. Data center operators must limit and monitor physical access to systems. Our Texas 1 facility has eight layers of security, including gated access, badged entry, biometric authentication, a bullet-proof mantrap and CCTV cameras that record 24×7. The site is monitored 24x7x365 by our own onsite security staff, not third-party vendors.
Camera Surveillance
Our cameras constantly monitor anyone entering or exiting data halls. They also monitor every section of the data halls. Videos are time stamped and we maintain detailed logs so customers can request footage of anyone in their deployment at any given time.
Security Policies & Procedures
Our security policies and procedures are strictly documented, as required by PCI. Data Foundry has a strict procedure for identifying and authorizing visitors to our facilities. No one is granted access without current identification and prior authorization. All onsite personnel and visitors receive unique IDs. We maintain a log of all visitors and employees entering and exiting the facility.
We have strict procedures for identifying and authorizing access by visitors and staff. Employee access must be authorized, and it is based on job function. Employees that have access to data halls are only those with a legitimate business need to do so. Employees must badge in at the gate and in the lobby, and they must also complete two-factor authentication when navigating the facility’s hallways and data halls. We revoke employee access immediately upon termination, and visitors’ passes are confiscated upon departure from the facility.
Tour Texas 1
Want to see Texas 1’s security features for yourself? Schedule a tour anytime to learn more about this world-class data center.